【CrackMe】Acid Burn
谨以此系列记录自己学破解的进程。
本文使用的CrackMe链接:【反汇编练习】160个CrackME索引目录1~160建议收藏备用 - 『脱壳破解区』 - 吾爱破解 - LCG - LSG |安卓破解|病毒分析|www.52pojie.cn
第一次玩crackme,先直接启动,熟悉一下各个界面。了解一下序列号出错的提示。
它有两种验证,一种是序列号+注册名,另一种是仅序列号,大致明白流程之后关闭,然后挂上x64dbg走起。
序列号
先从简单的下手,载入程序后搜索所有模块-字符串,搜索出错提示”Try Again!!”,然后跳转过去。
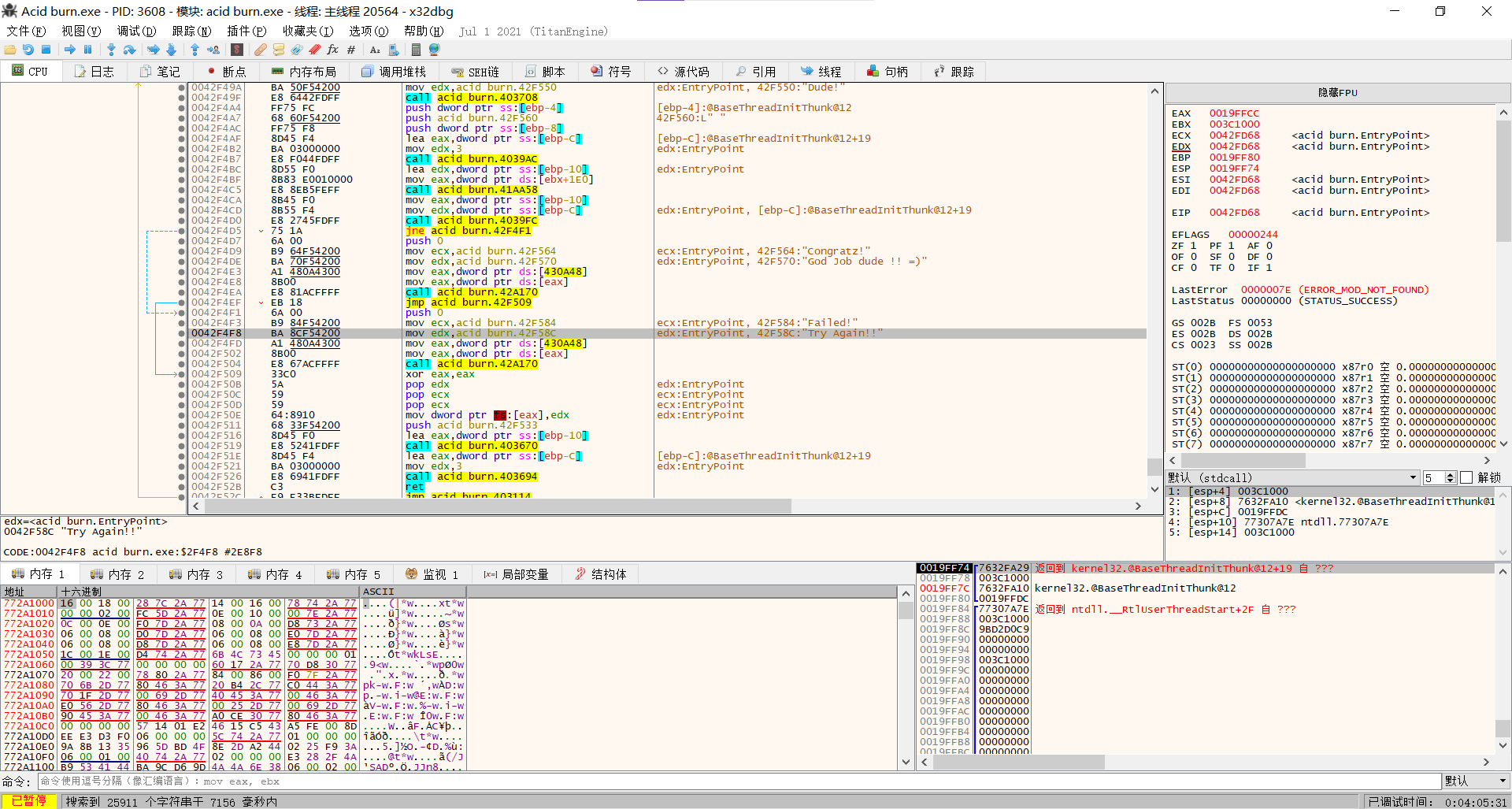
首先必须知道点汇编指令的含义,比如jmp是无条件跳转,jne是条件跳转之类的。
(其实也不用记,x64dbg用虚线箭头标出来的是条件跳转,实线是无条件跳转,
然后看到跳转过来的”Try Again!!”附近有一个虚线、一个实线箭头。
理清一下程序流程,首先它先对输入的数据进行判断,然后用jne判断是否符合,如果不符合就输出Fail,try again!!,如果符合就啥也不干。
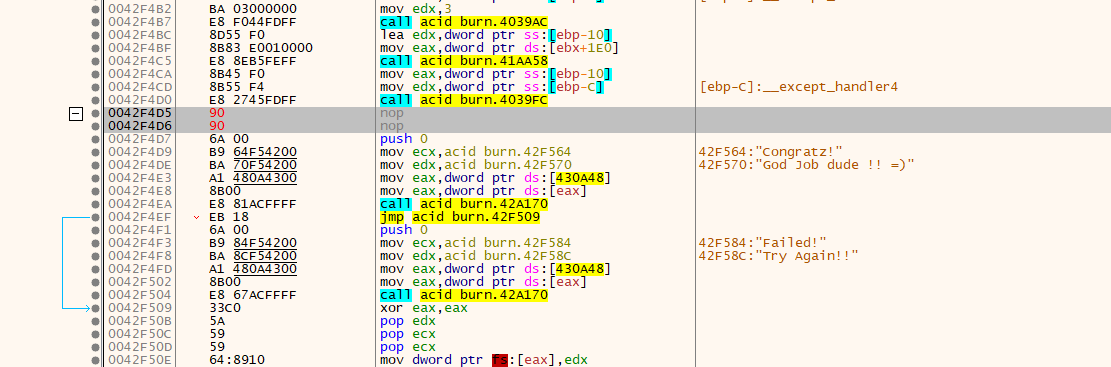
所以将jne指令用nop填充,第一个问题解决。
序列号+注册名
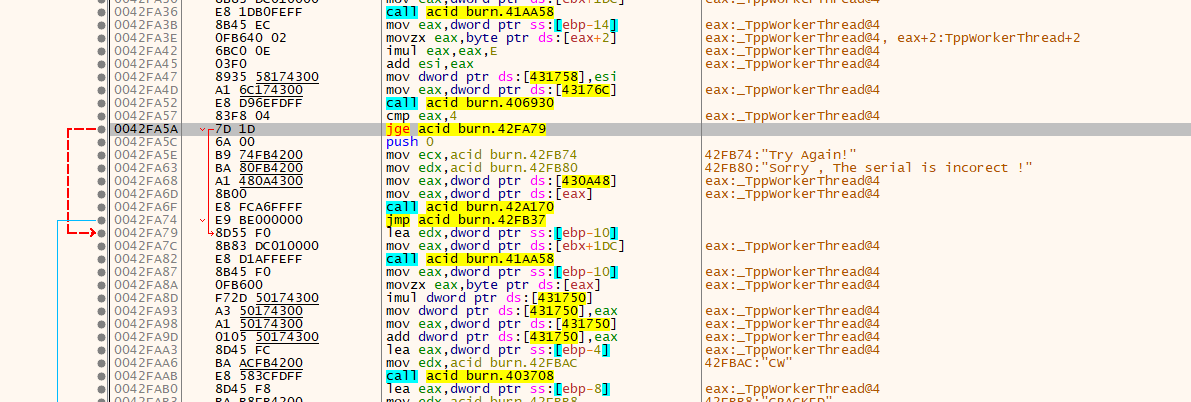
先用搜索字符串找到提示”Sorryxxxxxx”,会出现两个结果,因为它要对序列号和注册名判断两次,所以有两次提示。
先从第一处开始,jge也是条件跳转指令中一个,只要将jge改为jmp,这里就破解完成了。
然后找到第二处,
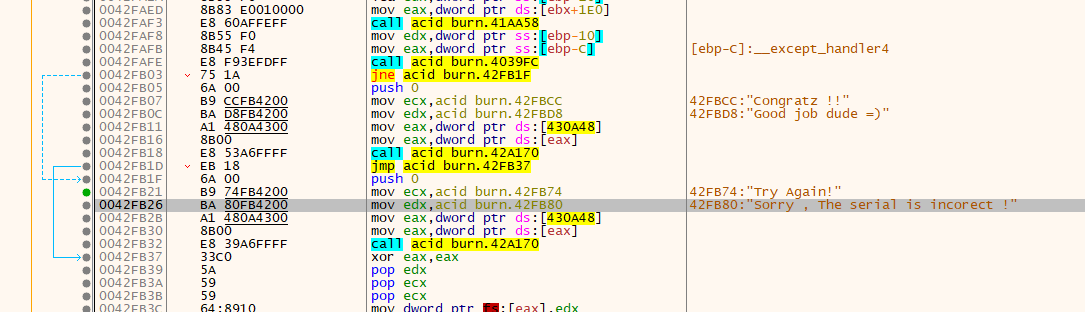
大致梳理一下流程,基本和之前一样,把条件跳转jne改为nop就行了
结尾
至此无论你输什么,都会显示祝贺成功。
最后可以输出修补程序,就是破解完的程序
This series documents my progress in learning reverse engineering.
Link to the CrackMe used in this article: 【Reverse Engineering Exercise】160 CrackME Index Directory 1~160 Recommend Save for Future Use - 『Unpacking and Cracking』 - 52PoJie - LCG - LSG |Android Cracking|Virus Analysis|www.52pojie.cn
First time playing with crackme, start by directly launching to familiarize myself with each interface and understand the error messages for incorrect serial numbers.
It has two validation methods: one for serial number + registration name, and another for serial number only. After roughly understanding the process, close it and launch x64dbg.
Serial Number
Starting with the simpler one. After loading the program, search all modules → strings for the error message “Try Again!!”, then jump there.

First, it’s essential to know the meanings of some assembly instructions, such as jmp being an unconditional jump and jne being a conditional jump.
(Actually, you don’t need to memorize; x64dbg marks conditional jumps with dashed arrows and unconditional jumps with solid arrows.)
Then, near where it jumps to “Try Again!!”, there’s one dashed arrow and one solid arrow.
Clarify the program flow: First, it evaluates the input data, then uses jne to check if it matches. If it doesn’t match, it outputs “Fail, try again!!”; if it matches, it does nothing.
So, fill the jne instruction with nop, and the first issue is resolved.

Serial Number + Registration Name
First, use the string search to find the message “Sorryxxxxxx”. Two results will appear because it checks both the serial number and registration name, so there are two messages.
Start with the first one. jge is also a conditional jump instruction; simply change jge to jmp, and this part is cracked.

Then find the second location.

Roughly outline the flow: it’s basically the same as before, change the conditional jump jne to nop.
Conclusion
Now, no matter what you input, it will display a congratulatory success message.
Finally, you can output the patched program, which is the cracked version.